Access logs are an Enterprise Edition-only feature.
What are Access Logs?
Access logs capture authentication events when users or API keys attempt to access a resource. They record whether the authentication was successful or failed, along with contextual information about the attempt. These logs are useful for:- Monitoring authentication patterns and login attempts
- Tracking which users are accessing which resources
- Identifying failed authentication attempts for security analysis
- Understanding geographic distribution of access attempts
- Analyzing user agent and device information
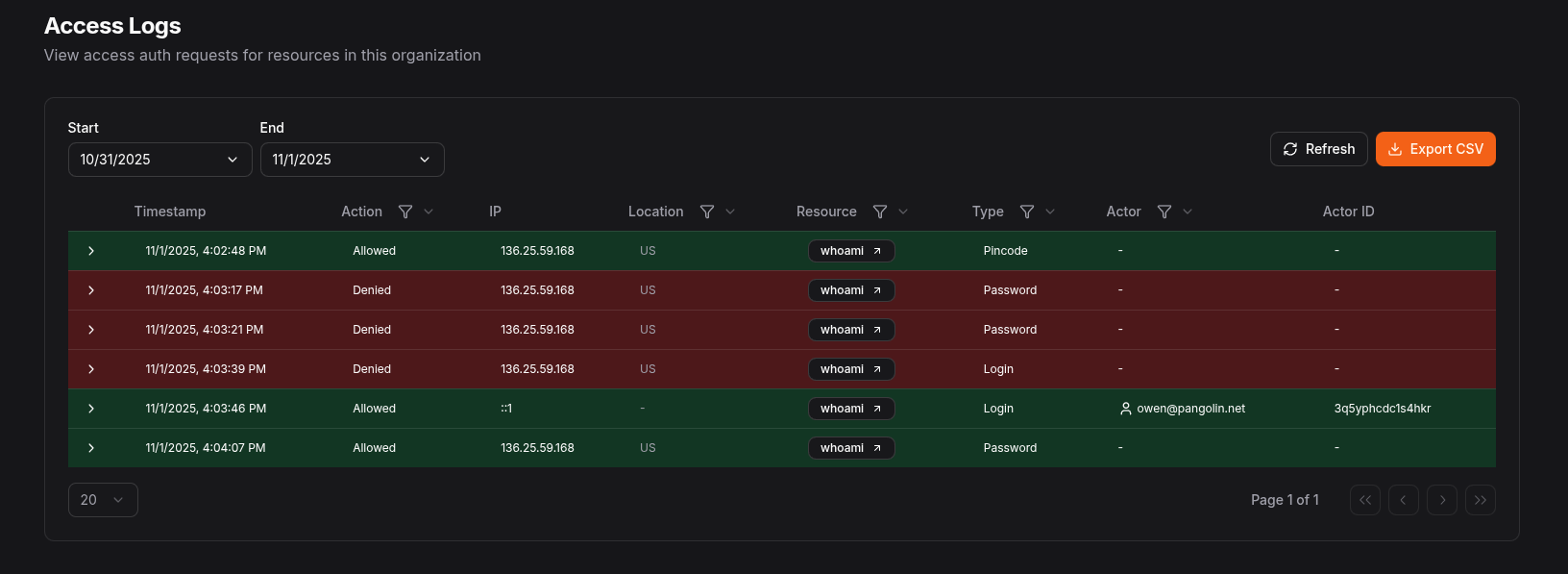
Access Log Fields
Each access log entry contains the following fields:| Field | Type | Description |
|---|---|---|
timestamp | number | Unix timestamp (in seconds) when the access attempt occurred |
action | boolean | Whether the access was allowed (true) or denied (false) |
type | string | The type of authentication event (e.g., “login”, “password”, “pincode”) |
actorType | string | The type of actor making the access attempt (“user” or “apiKey”) |
actor | string | The display name of the actor (username or API key name) |
actorId | string | The unique identifier for the actor (user ID or API key ID) |
resourceId | number | The ID of the resource being accessed (if applicable) |
ip | string | The IP address of the client making the access attempt |
location | string | The geographic location (country code) based on IP address |
userAgent | string | The user agent string of the client browser or application |
metadata | string | Additional contextual information in JSON format |

