Azure SSO is only available on Pangolin Cloud and Enterprise deployments. In enterprise, you must enable
use_org_only_idp in your private config file privateConfig.yml.How to create and set up an App Registration in Microsoft Azure from scratch
How to create and set up an App Registration in Microsoft Azure from scratch
Create an App Registration
In Azure, go to “Microsoft Entra ID”. Under “Manage”, click “App registrations”. On the “All applications” tab, select “Register an application”.Give it a name like “Pangolin”, select your preferred supported account types, and click “Register”. Leave the redirect URI blank for now; we will come back to this.Copy Credentials
On the new app registration, select the “Overview” tab. Here, you can copy the “Application (client) ID” and save for later.Now we need to generate the client secret. Click “Add a certificate or secret”. Then click “New client secret”. Enter a description like “Pangolin credentials” and choose an expiration time. Note that once this secret expires, you will need to generate a new one and replace it in the Pangolin dashboard for the associated IdP.Copy the “Value” field and save for later.We will revisit the Authorised redirect URIs field later, as we do not have Pangolin set up for Azure yet.
Creating an Azure Entra ID IdP in Pangolin
In Pangolin, go to “Identity Providers” and click “Add Identity Provider”. Select the Azure Entra ID provider option.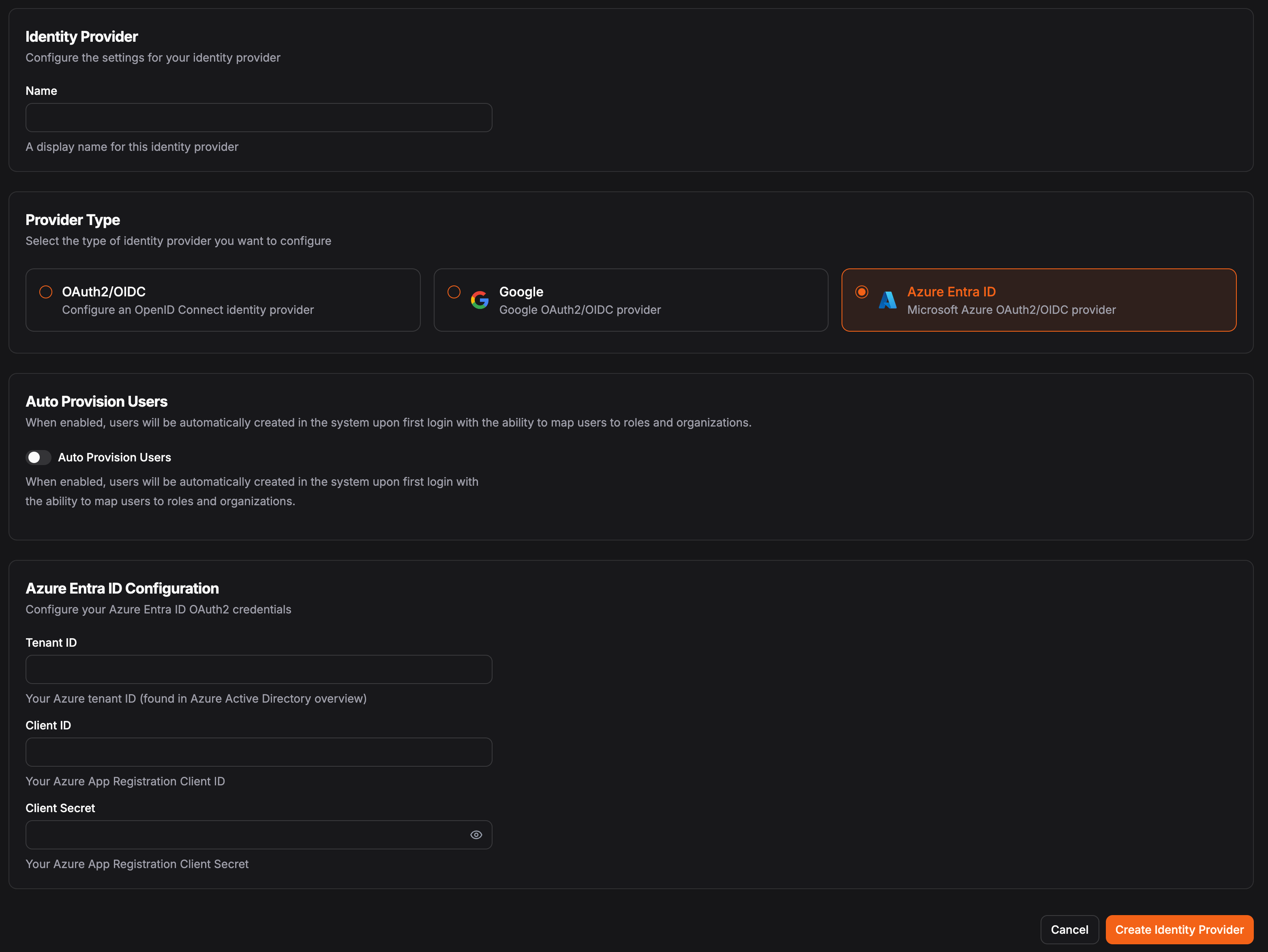
The application (client) ID from the “Overview” section of your app registration
The client secret value from the “Certificates and secrets” section of your app registration

